Ready, steady, scale
Environments are virtual private clouds configured with all of the subnets, gateways, and clusters you need to deploy your applications. Your VPC is ready to adapt at any time, regardless of your initial availability needs and release grade.
Development
Fastest deploys, lowest cost
Staging
Production parity, low cost
Production
Extended log retention, reliable uptime
Well-architected
Built on AWS Well-Architected Framework principles. Subnet configuration and selection that scales. Region and release grade-specific CIDR block allocation.
Dual-stack
Communicate over IPv6 and IPv4. FlexStack environments are future-proof and more cost-efficient than traditional IPv4 VPCs.
Architecture automation
Don't need a load balancer? Don't pay for one. FlexStack environments autoscale based on your usage.
Highly available
Two-nines? Three-nines? Four-nines? You set your availability target, we'll handle the rest.
Secure by default
Built-in resource access controls, zero-config database access, and enhanced network security for cautious teams.
Change is inevitable
FlexStack environments are designed to adapt to your needs. Whether you're rapidly growing your service count, looking for higher availability, or want to promote an environment to production, FlexStack has you covered. We make it simple to change your environment when your goals change – without downtime.
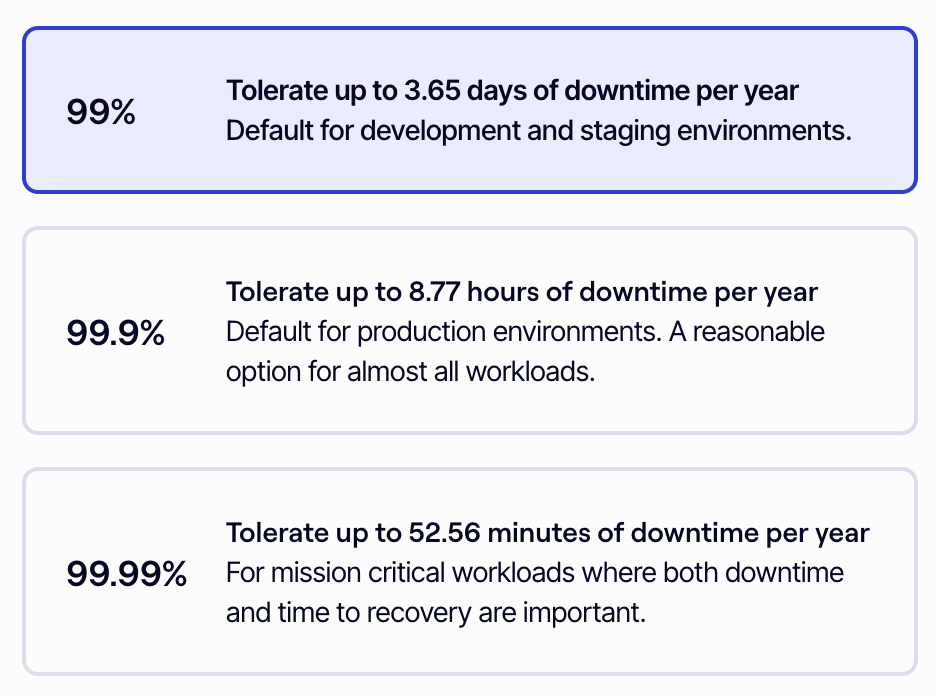
Target availability
Availability refers to the uptime and reliability of your services, often expressed as a percentage (e.g., 99.9% uptime, or three-nines). Actual availability is a function of your environment's design and the services you deploy, but FlexStack will help you meet your target.
Release grades
Release grades are a way to configure your environments based on their intended use. For example, you might have a development environment that's optimized for fast deploys and low cost, or a production environment that's designed for high availability and reliability.
Development
Optimize for early-stage application development and testing. Focus on cost-efficiency, deploying cheaper resources. Configure log retention, metric reporting, and alert thresholds with cost-savings in mind.
Staging
Create intermediate environments between development and production that closely mirror production. Use staging to test new features, integrations, and configurations before deploying to production while keeping costs low.
Production
Optimize for high availability and reliability. Configure production environments to handle changes to service workload and ensure consistent uptime. Retain logs and metrics for 90 days, so you can analyze performance and troubleshoot issues. Use production environments to host your customer-facing applications and services.
Patterns to build a fortress
Environments are configured to make security effortless. With built-in resource access controls, zero-config database access, and enhanced network security, you can be confident that your applications are set up to protect your data and your users.
Enhanced network security
For certain production use cases where security and isolation are paramount, FlexStack provides the flexibility to deploy services exclusively on private subnets.
Better security, effortless savings
In production environments, we provision a NAT gateway provider that
is managed by AWS. For Development and Staging environments, the
enhanced security option uses a t4g.nano NAT instance
in a single availability zone instead.
Resource RBAC
At FlexStack we love patterns that make security easier. Use tags to control access from FlexStack services to other AWS resources in your account that support tagging – from EC2 instances, SNS topic, and S3 buckets to IAM roles.
Tag-based access controlsOne tag is worth a thousand permissions
FlexStack adds tags to your resources that describe the project,
environment, and component they belong to, for example FlexStack:ComponentID. When you add these magic tags to your
AWS resources, service roles stipulate that they may access that
resource.
Read-only or full-access
FlexStack service roles are designed to be as restrictive as possible. You can assign resources a role that only allows read-only access, or a role that allows full access to the resource from a FlexStack service.
Zero-config database access
We've made it simple to integrate RDS and other AWS managed database solutions with your FlexStack services. With zero-config database access, you can connect to your database without needing to manage your own network security groups.
Databases guideInfrastructure as code
Use FlexStack to bootstrap your infrastructure as code journey. Environments are fully importable by Terraform, CDK, and other IaC tools cutting out the boilerplate and getting you to the good stuff faster.
Terraform
Data sources make it easy to reference FlexStack resources. We've fully documented our VPC, subnet, and security group exports so you can easily import them into your Terraform projects. Use the FlexStack API to list an environment's outputs and resources.
